Delving into which type of software enables centralized administration of mobile devices, this introduction immerses readers in a unique and compelling narrative. With a focus on different software solutions like MDM, EMM, and UEM, we explore the key features required for efficient administration, implementation considerations, and crucial security aspects. Let’s unravel the complexities of mobile device management together.
Types of software for centralized administration of mobile devices: Which Type Of Software Enables Centralized Administration Of Mobile Devices
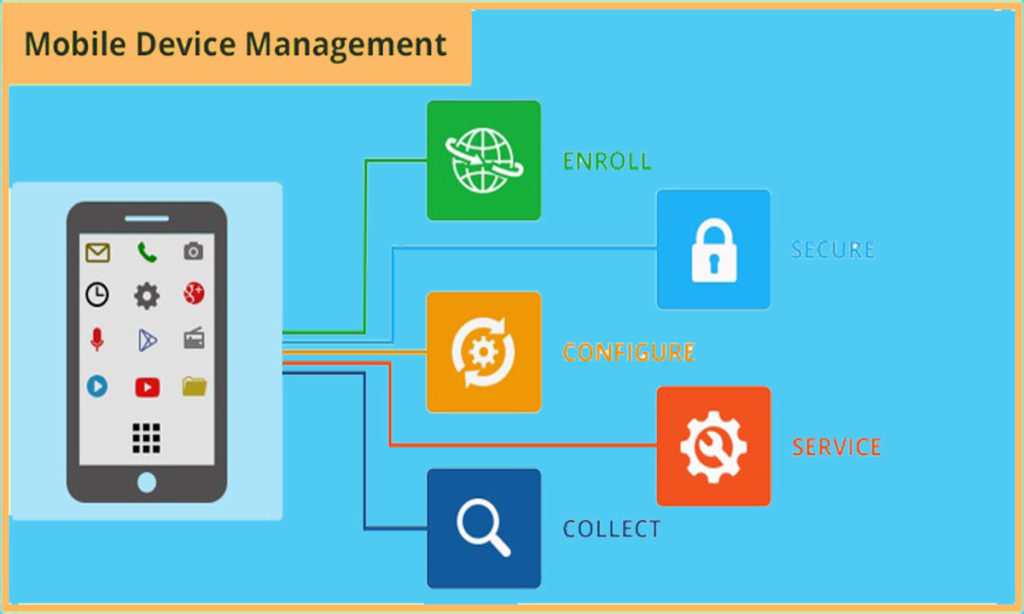
Centralized administration of mobile devices is crucial for businesses to ensure security, compliance, and efficiency. There are different types of software solutions available to streamline this process, including Mobile Device Management (MDM), Enterprise Mobility Management (EMM), and Unified Endpoint Management (UEM) software.
Mobile Device Management (MDM)
MDM software focuses on managing, securing, and monitoring mobile devices within an organization. It allows IT administrators to enforce policies, push updates, and remotely wipe devices if needed. Popular examples of MDM software include AirWatch by VMware, MobileIron, and Microsoft Intune. The benefits of MDM software include enhanced security, compliance management, and improved device performance. However, MDM may have limitations when it comes to managing multiple device types or providing a seamless user experience.
Enterprise Mobility Management (EMM)
EMM software goes beyond MDM by also incorporating mobile application management, identity management, and content management. It provides a more comprehensive approach to managing mobile devices and applications in an enterprise environment. Leading EMM solutions include IBM MaaS360, Citrix Endpoint Management, and BlackBerry UEM. EMM software offers the advantage of increased productivity, seamless integration with existing systems, and improved user experience. However, the complexity and cost of EMM solutions can be a drawback for some organizations.
Unified Endpoint Management (UEM)
UEM software takes a holistic approach to managing all endpoints, including mobile devices, desktops, laptops, and IoT devices, from a single console. It combines the features of MDM and EMM to provide a unified management solution for all endpoints in an organization. Top UEM solutions include VMware Workspace ONE, Ivanti Endpoint Manager, and BlackBerry UEM. UEM offers the benefits of simplified administration, consistent security policies, and increased operational efficiency. Nevertheless, the implementation and integration of UEM software can be challenging for some organizations.
Key features required for centralized administration of mobile devices

Centralized administration of mobile devices requires specific key features to ensure efficient management and security. Let’s explore the essential features that a software solution must have to enable centralized administration of mobile devices.
Remote Device Management, Which type of software enables centralized administration of mobile devices
Remote device management is a crucial feature that allows administrators to monitor and control mobile devices from a centralized location. This feature enables tasks such as software updates, configuration changes, and troubleshooting to be performed remotely, saving time and resources.
Application Deployment
Application deployment is another essential feature that simplifies the process of distributing and updating applications on mobile devices. Administrators can push new applications, updates, or patches to multiple devices simultaneously, ensuring all devices are up to date with the latest software.
Security Policies
Security policies play a critical role in centralized administration by allowing administrators to enforce security measures across all mobile devices. Features like device encryption, password requirements, and remote data wiping help protect sensitive information and prevent unauthorized access.
Compliance Monitoring
Compliance monitoring ensures that mobile devices adhere to organizational policies and regulations. Administrators can track device usage, monitor security settings, and generate reports to ensure compliance with industry standards and data protection laws.
Scalability and Flexibility
Scalability and flexibility are key features that allow software solutions to adapt to the growing needs of an organization. The ability to manage a large number of mobile devices efficiently and scale operations as needed is essential for centralized administration.
In real-world scenarios, these key features play a critical role in mobile device administration. For example, a company with a large fleet of mobile devices needs remote device management to troubleshoot issues quickly and ensure devices are functioning properly. Application deployment allows IT teams to deploy new software seamlessly, while security policies and compliance monitoring help maintain data security and regulatory compliance.
Implementation and deployment considerations for centralized administration software
When implementing centralized administration software for mobile devices, organizations need to consider several key factors to ensure a smooth deployment process and seamless integration with existing IT infrastructure.
Steps involved in implementing centralized administration software
- Assess organizational needs and requirements for centralized administration of mobile devices.
- Research and select a centralized administration software solution that aligns with the organization’s needs.
- Plan the implementation process, including setting up user accounts, defining policies, and configuring security settings.
- Conduct thorough testing of the software before full deployment to identify any potential issues.
- Train IT staff and end-users on how to use the centralized administration software effectively.
Best practices for deploying software solutions across different operating systems and device types
- Ensure compatibility of the centralized administration software with various operating systems and mobile device types.
- Develop a deployment strategy that takes into account the specific requirements of each operating system and device type.
- Use mobile device management (MDM) tools to streamline the deployment process and manage devices efficiently.
- Regularly update the centralized administration software to ensure compatibility with new operating system versions and device models.
Ensuring seamless integration with existing IT infrastructure
- Conduct a comprehensive assessment of the organization’s current IT infrastructure to identify any potential compatibility issues.
- Integrate the centralized administration software with existing systems, such as directory services and network infrastructure, to ensure seamless operation.
- Implement protocols for data syncing and backup to prevent data loss and ensure data integrity during integration.
Tips for troubleshooting common deployment issues
- Regularly monitor the centralized administration software for performance issues and address them promptly.
- Provide ongoing support and training to IT staff and end-users to address any user-related deployment issues.
- Establish a feedback mechanism to gather input from users and IT staff for continuous improvement of the deployment process.
Security considerations when using software for centralized administration of mobile devices
When it comes to managing mobile devices centrally, security is a critical aspect that organizations cannot afford to overlook. The increasing use of mobile devices for work purposes has brought about various security challenges that need to be addressed effectively.
Security Challenges Associated with Managing Mobile Devices Centrally
- Lack of physical control over devices
- Insecure network connections
- Data leakage and unauthorized access
- Device theft or loss
Addressing Data Protection, Encryption, Authentication, and Compliance Requirements
Software solutions for centralized administration of mobile devices play a crucial role in ensuring data protection, encryption, authentication, and compliance with regulations. These solutions offer:
- Data encryption: Protects sensitive information stored on devices.
- Authentication mechanisms: Ensure only authorized users can access the devices and corporate data.
- Compliance features: Help organizations adhere to industry regulations and standards.
Role of Mobile Threat Defense Solutions
Mobile threat defense solutions are specifically designed to enhance the security of centrally managed devices by:
- Detecting and preventing mobile threats: Malware, phishing attacks, and other mobile-specific threats.
- Real-time threat monitoring: Constantly monitoring device activities for any suspicious behavior.
- Secure access controls: Implementing access controls to prevent unauthorized access to corporate resources.
Recommendations for Strengthening Security Posture
- Implement strong password policies: Enforce complex passwords and regular password changes.
- Enable remote wipe capabilities: Allow for remote data wipe in case of device loss or theft.
- Regular security audits: Conduct periodic security audits to identify vulnerabilities and gaps.
Last Recap
In conclusion, understanding the nuances of software solutions for centralized administration of mobile devices is essential for organizations looking to streamline their mobile device management processes. By prioritizing key features, implementation best practices, and stringent security measures, businesses can ensure a seamless and secure mobile device environment. Embracing the right software is the first step towards efficient and centralized mobile device administration.
Answers to Common Questions
What are the main differences between MDM, EMM, and UEM software?
MDM focuses on managing specific devices, EMM incorporates application and data management, while UEM offers a unified approach to managing all endpoints.
How do scalability and flexibility impact centralized administration software for mobile devices?
Scalability ensures the software can handle a growing number of devices, while flexibility allows for customization based on organizational needs.
